What is DLL Injection?
DLL injection is a process of hiding malicious activity under another legitimate Windows process, which can be considered malware using Windows process as a cloak and avoiding being busted. Malicious software force to load its own DLL which is of course malicious too, and makes it a subprocess of a legitimate, totally usual process’ child process. It can be any process, like svchost.exe or explorer.exe.
For now we know that malware will inject a subprocess under a usual process and try to hide its activity and avoid being busted. But as a foundation we need to know what is DLL exactly, what DLLs stand for. DLL which is short for Dynamic-Link Library is provided by Microsoft for Windows applications to share code among multiple applications. In programming languages we know libraries used for making coding easy and previously defined functions will help us while we are coding; in Windows every program uses need to execute some basic operations and they use DLL for this function. Big operations need basic operations and programs uses pre-defined functions provided by DLL for these actions. We all heard Windows API (Application Programming Interface) before, you can think DLLs are the most basic block of Windows API. For example:
-
kernel32.dll — access and manipulation of files and folders.
-
gdi32.dll — used for displaying and manipulating graphics.
-
ntdll.dll — interface to windows kernel.
-
wsock32.dll — used by Internet and network applications to handle network connections.
In-Depth:
Malware creates DLL or writes path of malicious DLL inside a remote process using Windows API functions. When target.exe executed, “target.exe” will call the required DLLs from defined paths and load them. By this technique totally normal application will execute “mal.dll” and shows it is a normal subprocess of totally normal application.
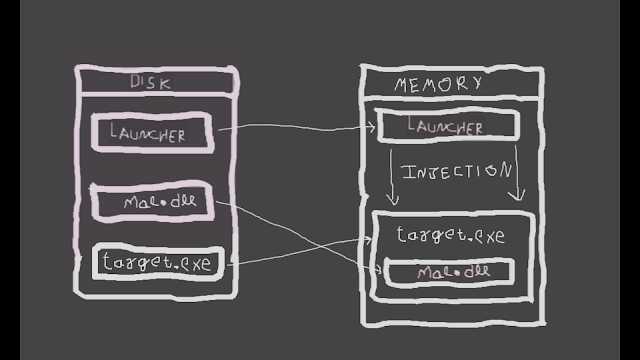
As shown in the above picture, we have a launcher file which will be responsible for performing injection of malicious DLL into the target victim executable , mal.dll and target.exe present on the disk. Whenever target.exe is executed, mal.dll is also executed. This technique is a type of covert malware launching technique used for hiding malicious activities inside a legitimate process which is target.exe in our case.
How it is achieved?
Problem for malware — Process specific firewall, in order to bypass this firewall, there are certain steps to get access to target.exe.
- Preparing the path of mal.dll
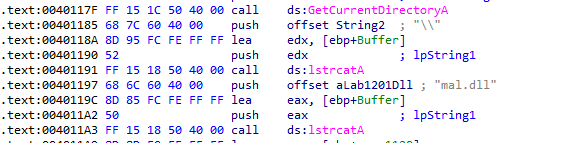 First, malicious software which we gonna call as the launcher uses GetCurrentDirectoryA to get the current working directory and uses lstrcatA function twice to prepare the path of mal.dll, for example: *C:\Users\user_name\directory\mal.dll*
First, malicious software which we gonna call as the launcher uses GetCurrentDirectoryA to get the current working directory and uses lstrcatA function twice to prepare the path of mal.dll, for example: *C:\Users\user_name\directory\mal.dll*
- Retrieving PID of target.exe
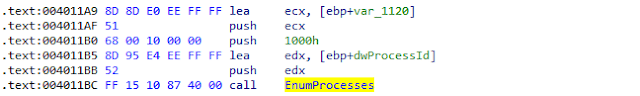
The next step is to retrieve the process id of target.exe, EnumProcesses is a function that retrieves the process identifier for each process object in the system and stores them into an array, after which the launcher can traverse that array and do the string comparison of string “target.exe” with the name of the processes associated with a PID in that array and loop until the correct PID is found.
- Obtain handle to the target.exe
Once the PID is retrieved, it can be used as a parameter to OpenProcess function to obtain a handle to target.exe.
- Allocate memory inside the virtual address space of target.exe
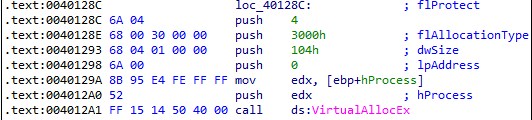
VirtualAllocEx- This function allocates memory inside target.exe using the handle (hProcess) retrieved from the previous step.
- Write mal.dll full path at newly created memory in the previous step.
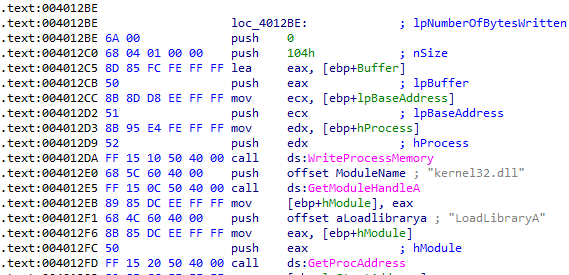
In this code, the Buffer parameter point to a string which contains the full pathname to mal.dll, lpBaseAddress is the starting point of newly created memory and hProcess contains a handle to target.exe. Then WriteProcessMemory function is called to write the Buffer at lpBaseAddress which means that the directory path of mal.dll is now written inside *target.exe.*In order to execute DLL, LoadLibraryA function from kernel32.dll is needed, therefore it manually resolves the address of LoadLibraryA and stores it into a variable.
- Execution
Finally, CreateRemoteThread is called which creates a thread that runs in the virtual address space of target.exe eventually executing mal.dll.
Above shown example is one of the ways through which DLL injection can be achieved, but it is not limited to a single approach.